Blog
Choosing a visitor management system part 2: What do you want it to DO?
by Andrew Jones

This is the second of three articles about choosing a visitor management system.
What do you want your visitor management system to do? The answer sounds obvious, doesn’t it? You want it to manage your visitors. But not all visitor management systems perform the same tasks, so it’s worth thinking about what those tasks are and if they are important to you.
Identification
Do you know everybody at work? If you do, you can tell the employees from the visitors. If you don’t, a stranger you encounter could be anybody. Either way, if they aren’t wearing a visitor badge, you may wonder who they are and what they are doing there.
The table below lays out eight scenarios where you encounter a stranger at work. Who you think the stranger is depends on two basic things: (1) what your organization’s visitor badge policy is and (2) whether or not the stranger is actually wearing a visitor badge.
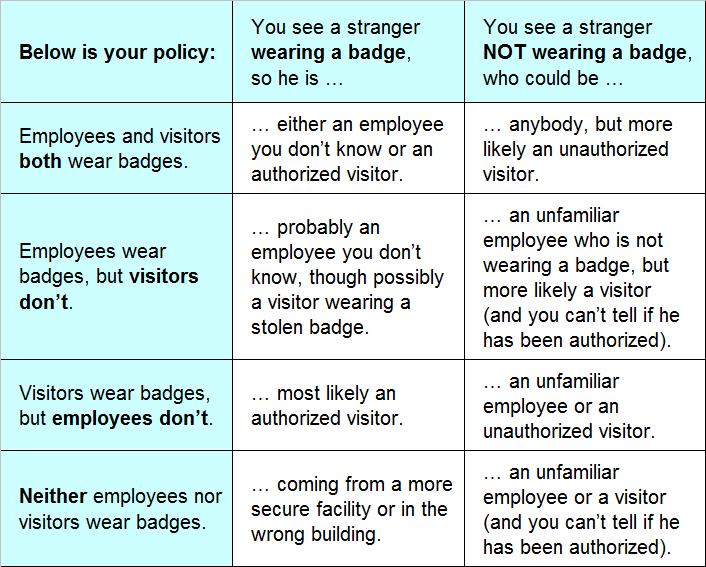
As you can see, the less an organization relies on identifying its building’s occupants, the more mystery there is about their identity. At best, not identifying visitors arouses employees’ curiosity and, at worst, leaves people and property exposed to potential harm.
A good visitor management system, in conjunction with the policies it supports, should be able to tell you who has permission to be in your facility, as well as who does not.
Tracking
Whether you work in a school, a hospital, a business, or a government or non-profit agency, the occupants of your building fall into four distinct categories:
1. People who are there full time and permanently (employees, students, and patients, clients, or residents, such as in an assisted-living facility)
2. People who are there full time and temporarily (contractors, temporary help, and substitute teachers)
3. People who are there part time and frequently (vendors and volunteers)
4. People who are there infrequently or just once (visitors, including family members and clergy, and students on a field trip)
The first category above falls out of the scope of most visitor management systems. But it is good policy to know, at all times, which of these people are in your building and, better yet, where these people are in your building. In an emergency evacuation, everyone needs to be accounted for.
Background
The more sophisticated your visitor management system and policy are, the better you can verify that a visitor is who he says he is. Asking him to produce some government-issued identification, like a driver’s license, is a good start. But some organizations — especially those, like schools, with vulnerable occupants — require more information about their visitors. This can be accessed through online databases, as well as from an audit trail maintained by your own computerized VMS.
Record-keeping and Reporting
While a VMS’s tracking capability let’s you know who is (or isn’t) in your facility now, its record-keeping and reporting function should tell you who was in your facility, as well as when, how often, and who they visited. This helps complete a visitor’s background (was there any trouble last time?) and provide evidence for liability or confidentiality issues. For schools and hospitals, a “watch list” can help identify potential custodial issues.
Previously:
Choosing a visitor management system — part 1: Five basic criteria
Next:
Choosing a visitor management system — part 3: Not all badges are made alike
Also:
Pro’s and Con’s of a Manual Visitor Sign-In System
Pro’s and Con’s of an Electronic Visitor Management System
Want the latest, best security practices delivered straight to your inbox? Enter your email address in the "Subscribe" area (on the left side navigation).
Download Free Whitepaper ›
Our exclusive "Guide to Choosing a Visitor Management System"
Follow us on Social Media for more security content.![]()
![]()
![]()
Posted on 5/28/2015



 Paul Kazlauskas
Paul Kazlauskas
 Andrew Jones
Andrew Jones